Navigating and implementing HIPAA compliance for healthcare providers can be complex, overwhelming, and demanding at the same time. However, it’s essential for anyone with access to patient information to understand and comply with this vital legal and ethical framework. SAAS solutions like AffableBPM offer a secure document repository, granting authorized users access to the information relevant to their roles. To address common misconceptions and questions, we’ve created this article to provide a clear and concise guide to HIPAA standards and provisions.
In a nutshell, HIPAA, which stands for Health Insurance Portability and Accountability Act, was enacted in 1996 to modernize healthcare information flow and protect patient medical data. Here are the key aspects of HIPAA:
HIPAA comprises five titles:[1]
In essence, HIPAA safeguards patient information, preventing misuse, theft, or embezzlement of personal healthcare data.
“Covered entities are defined in the HIPAA rules as (1) health plans, (2) health care clearinghouses, and (3) health care providers who electronically transmit any health information in connection with transactions for which HHS (Health and Human Services) has adopted standards. Generally, these transactions concern billing and payment for services or insurance coverage.” [2]
A “business associate” refers to an individual or organization that performs specific functions or activities involving the use or disclosure of Protected Health Information (PHI) on behalf of a covered entity. [3] Examples of business associates include lawyers, accountants, IT contractors, billing companies, cloud storage services, and email encryption services, among others. Before accessing PHI, a business associate must sign a Business Associate Agreement with the covered entity. This agreement outlines the specific PHI they can access, how it should be used, and the requirement to return or destroy the information once the task is completed. While in possession of PHI, the business associate shares the same HIPAA compliance obligations as a covered entity.
4 Key HIPAA Compliance Guidelines for Healthcare Providers are as follows:
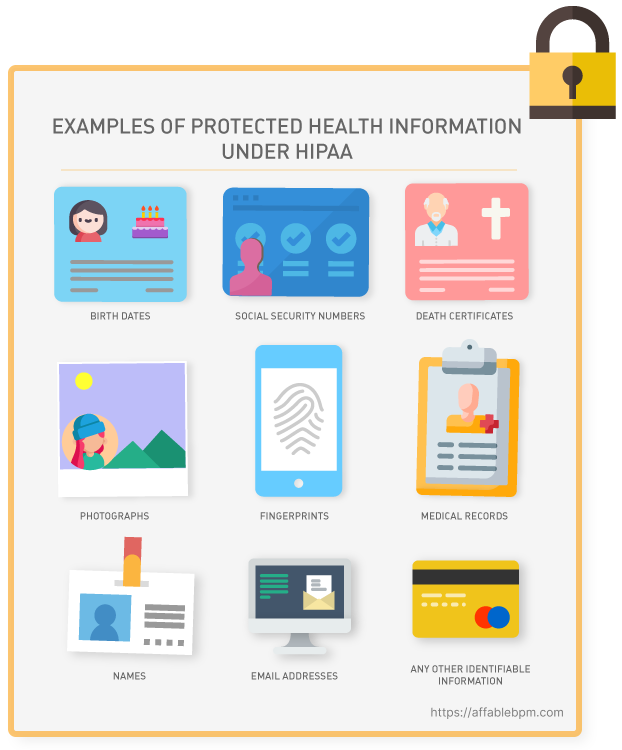
Under HIPAA privacy rules, healthcare providers are obligated to grant individuals access to their Protected Health Information (PHI), which encompasses health conditions, treatment plans, notes, images, lab results, and billing details. The privacy rule outlines the permissible uses and disclosures of PHI by healthcare professionals, lawyers, and other authorized entities. It applies to all forms of PHI, whether stored or transmitted electronically, on paper, or through oral communication by a covered entity or its business associates.
The HIPAA Security Rule works hand-in-hand with the Privacy Rule to establish the necessary national standards for covered entities in handling electronic Protected Health Information (ePHI). This rule focuses on safeguarding ePHI through various measures. “The Security Rule requires appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of ePHI.” [4]
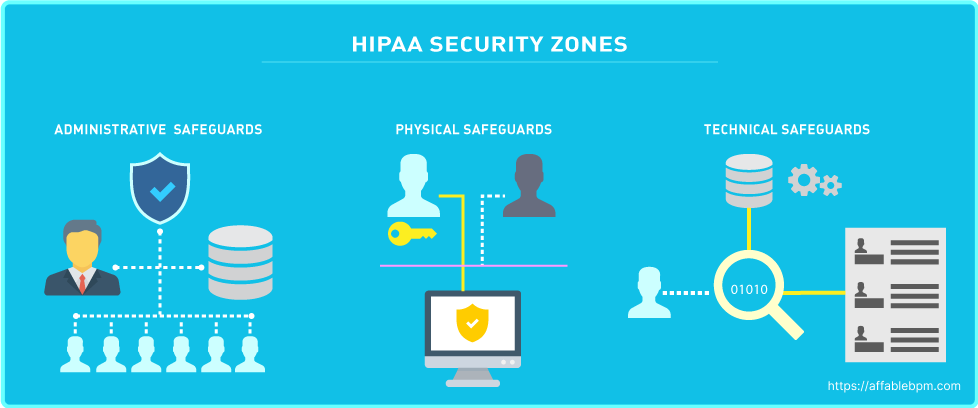
The HIPAA Security Rule consists of three categories with specific standards, which are detailed below: [5]

Under the HIPAA Breach Notification Rule, covered entities are obligated to inform individuals within 60 days if there has been unauthorized access to their PHI. It’s important to note that even if ePHI is encrypted by ransomware, it is still considered a breach and falls under this rule. If the breach affects more than 500 PHI records, the covered entity must notify the Department of Health and Human Services, which may involve the Office for Civil Rights (OCR). Additionally, in such cases, the covered entity is required to issue a press release about the breach to inform the public. [10]
The Enforcement Rule outlines the compliance responsibilities of covered entities in terms of cooperation during the enforcement process. When individuals or organizations report HIPAA violations to the Office for Civil Rights (OCR), the OCR is responsible for investigating and reviewing those reported violations. The Enforcement Rule sets forth guidelines for determining the amount of civil penalties in case of a violation and establishes procedures for hearings and appeals if a covered entity contests a violation determination. It ensures a fair and structured enforcement process for addressing HIPAA violations and resolving disputes.
Covered entities should be aware of the following penalties as per the violation tier:[12]
Fines for HIPAA violations are assessed based on various factors, including the category of violation, the number of records exposed in a breach, the level of risk associated with the data exposure, and the degree of negligence demonstrated. The maximum fine per year for the most serious Tier 4 violation can reach up to $1,919,173. In cases of willful neglect, criminal charges can also be filed. Additionally, victims of a breach have the option to pursue civil lawsuits to seek damages. The entities most commonly subject to enforcement include private medical practices, hospitals, outpatient facilities such as pain clinics or rehabilitation centers, insurance groups, and pharmacies. It is crucial for these organizations to prioritize HIPAA compliance to mitigate the risk of penalties and legal consequences.
HIPAA requirements can be violated in various ways, with the most common being negligence or incomplete compliance, leading to data breaches, unauthorized release ofPHI, or access by unauthorized employees. HIPAA violations can persist for extended periods, often going unnoticed for months or even years. The penalties for such violations increase as their duration extends. Therefore, it is crucial for HIPAA-covered entities to conduct regular compliance reviews to proactively identify and address any potential violations before they are discovered by regulatory authorities.
There are three main ways that HIPAA violations are discovered: [11]
Even in cases where a data breach does not directly involve a HIPAA violation or a complaint is found to be unfounded, the Office for Civil Rights (OCR) may still uncover unrelated HIPAA violations during their investigations. If such violations are discovered and deemed significant, they may lead to the imposition of financial penalties or other enforcement actions. [11]
Within the HIPAA regulations, there is a notable absence of specific guidance on the content and components of a HIPAA risk assessment. However, the Department of Health and Human Services emphasizes that the purpose of a HIPAA risk assessment is for a Business Associate to proactively evaluate their organization internally and identify potential vulnerabilities, threats, and risks related to PHI they handle. While the exact approach may vary depending on the organization, here are some common objectives of a HIPAA risk assessment:
“The HIPAA risk assessment, the rationale for the measures, procedures, and policies subsequently implemented, and all policy documents must be retained for a minimum of six years.” [12]
HIPAA compliance is about fostering trust with customers by safeguarding their data. Compliance with HIPAA is an ongoing commitment, requiring continuous efforts rather than a one-time assessment. It is essential for Covered Entities and Business Associates to remain vigilant in their understanding and implementation of HIPAA requirements. Healthcare solution such as AffableBPM, based on HIPAA compliant Microsoft Azure services, make contractual assurances about data safeguarding, reporting including breach notifications and data access in accordance with HIPAA. [13] Seeking professional advice is highly recommended if any aspect of HIPAA raises concerns or uncertainties. Ignorance of HIPAA does not serve as an excuse for noncompliance, and the responsibility to comprehend, adopt, and maintain HIPAA guidelines is significant. Prioritizing compliance is crucial for the long-term success and reputation of organizations handling PHI.
References >
[1] https://www.dhcs.ca.gov/formsandpubs/laws/hipaa/Pages/1.10HIPAATitleInformation.aspx
[2] https://privacyruleandresearch.nih.gov/pr_06.asp
[3] https://www.hhs.gov/hipaa/for-professionals/privacy/guidance/business-associates/index.html
[4] https://www.hhs.gov/hipaa/for-professionals/security/index.html
[5] https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html
[9] https://www.hipaajournal.com/hipaa-compliance-checklist/
[10] https://www.hhs.gov/hipaa/for-professionals/breach-notification/index.html
[11] https://www.hipaajournal.com/common-hipaa-violations/
[12] https://www.hipaaguide.net/recent-hipaa-changes/
[13] https://learn.microsoft.com/en-us/azure/compliance/offerings/offering-hipaa-us